Integration in UltraSearch¶
The integration of DataCentral in UltraSearch is very simple.
You can either configure it manually in the UltraSearch UI or roll it out to multiple devices with a pre-built configuration.
Manual Configuration¶
To manually connect UltraSearch to your DataCentral, open UltraSearch and then select “Options” > “Miscellaneous” > “Connect with a DataCentral service”.
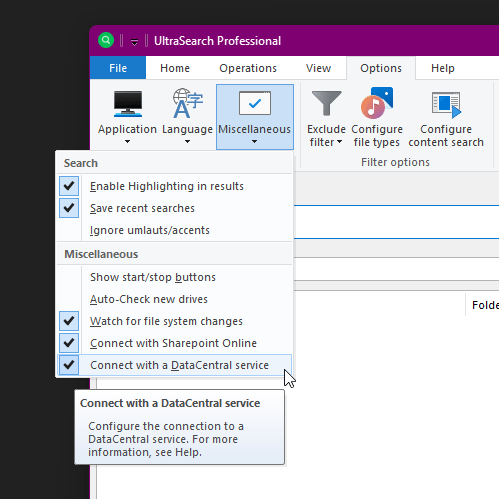
Here, a dialog opens in which you can enter the servername / IP address and the port under which you are hosting the DataCentral service.
Note
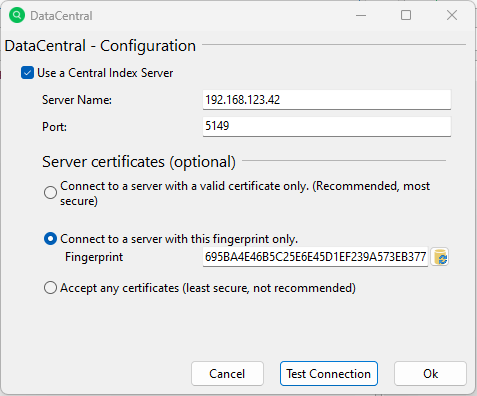
The default port for DataCentral communication is 5149. Please make sure that the specified port is open for incoming and outgoing traffic!
You can also choose a fitting option for server certificates here.
Connecting to a server with a fingerprint is the best compromise between security and practicality. For a quick setup, you can use this preselected option.
Note
The certificate settings are only confgurable in administration mode. In case UltraSearch was not started in administration mode, you can enable it via the “Change settings” button.
Roll-out on multiple Devices¶
For the roll-out of UltraSearch on multiple devices, you can specify these settings directly via the command line during installation. In this case, the end user does not have to configure it manually in UltraSearch.
Default settings for the DataCentral connection can be specified with the commands /DefaultIndexServerName and /DefaultIndexServerPort. Additionally, the option /VERYSILENT allows skipping all UI interaction within the setup.
Configuration of Certificates¶
The communication between UltraSearch and DataCentral requires using certificates.
Note
Certificates are essential for establishing trusted, encrypted connections between servers and clients, especially when dealing with sensitive data. By encrypting the connection with certificates, we prevent unauthorized parties from intercepting or “listening in” on data transmissions, ensuring data integrity and security.
How UltraSearch can accept Certificates¶
There are three different ways how UltraSearch can accept certificates.
Trust all¶
To begin with, you can configure to accept any certificate from the server. However, we do not recommend this method since this type of communication represents a potential security vulnerability!
Note
This method is especially useful for software evaluation purposes, for example during a trial phase.
Example command line parameter:
UltraSearch-Setup.exe /VERYSILENT /SUPPRESSMSGBOXES /PASSWORD=UltraSearch-license-key /IndexServerAcceptAnyCertificate True /DefaultIndexServerName hostname /DefaultIndexServerPort 5149
This is also configurable within the UltraSearch UI.
Accept only a Certificate with a specific Fingerprint¶
Accepting only certificates by their fingerprint allows verification of a certificate’s unique identifier without storing it on the device.
For self-signed certificates, this method ensures secure connections by matching the incoming certificate’s fingerprint with a trusted one, eliminating the need for external storage.
Example command line parameter:
UltraSearch-Setup.exe /VERYSILENT /SUPPRESSMSGBOXES /PASSWORD=UltraSearch-license-key /IndexServerCertificateThumbprint "5B359EE386EE5AA450216A80487968E6BA35DF86" /DefaultIndexServerName hostname /DefaultIndexServerPort 5149
This is also configurable within the UltraSearch UI.
Accept a Certificate from a specified Certificate File¶
Accepting a certificate from a specified file path means only the certificate stored there is considered trusted.
Example command line parameter:
UltraSearch-Setup.exe /VERYSILENT /SUPPRESSMSGBOXES /PASSWORD=UltraSearch-license-key /IndexServerCertificate "C:\path\certificate.pfx" /IndexServerCertificatePassword password /DefaultIndexServerName hostname /DefaultIndexServerPort 5149
Note
When installing UltraSearch without any of these certificate command line parameters, UltraSearch will validate the certificate via fingerprint by default. In this case, the first connection to the DataCentral service will obtain its fingerprint to UltraSearch. This fingerprint will be used for all further communication.
Executing a Search¶
When UltraSearch is configured to connect to DataCentral, it’s time to start the first search… Just use UltraSearch like it is normally used.
For all shares which are indexed with DataCentral you will recieve search results dirctly form the DataCentral service. Other shares and local drives will be handeld as usual and therefore don’t benefit from the DataCentral performance.
Tip
Using the “Suggested Paths” in UltraSearch will automatically (by default) search in shares indexed by DataCentral!
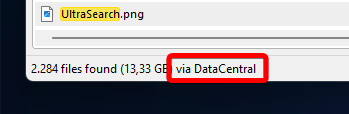
UltraSearch will indicate at the bottom left corner whether results are from DataCentral: